If you add a mod to WhatsApp, you can quickly get a Trojan on your smartphone.

in great shape
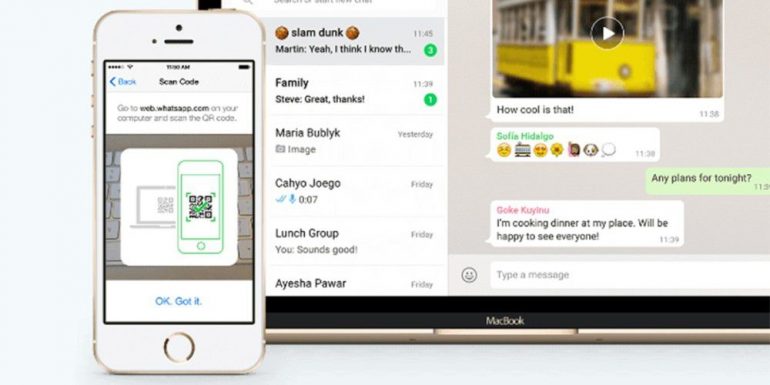
WhatsApp’s extensions can put the security of Android smartphones at risk.
© whatsapp.com
WhatsApp operators regularly add new functions to their messengers. If it doesn’t happen fast enough, you can fall back on unofficial extensions (the so-called mods). Well-known extensions are, for example, WhatsApp Plus, GBWhatsApp or FMWhatsApp. However, there is a huge security risk, especially in the latter expansion. Security researchers from Kaspersky found version 16.80.0 in FMWhatsApp extension
Trojaner Triada
. Malware apparently got into software through a manipulated Software Development Kit (SDK). Kaspersky may also have made a preliminary statement about the effects of the Trojan: Triada is collecting data about the device in the background, unnoticed. The Trojan is then downloaded via the Internet. Some of them display advertisements, others are paid subscriptions on behalf of the user. Other malware, however, logs into their own WhatsApp account, but they send SMS with confirmation codes unnoticed.
Anyone who has the current virus scanner installed on their Android device should have already been warned in the case of FMWhatsApp. Removal should also be possible. If you want to be sure that you will not be spied on, you should stay away from such extensions. WhatsApp operators also speak out against the use of the mod. In the worst case, the account can also be blocked by the WhatsApp operator. FMWhatsApp ensures that users can better customize the messenger as per their preferences. The mod has an anti-eraser function for messages. It can also be used to limit visibility to other users. In addition, two different phone numbers can be used.
More Exciting WhatsApp Topics

Internet fan. Alcohol expert. Beer ninja. Organizer. Certified tv specialist. Explorer. Social media nerd.